
We provide security for apps, data, identity, software licensing, digital content and cybersecurity solutions for a connected world
Aft India offers Copy Protection, Software Protection, USB Dongle, Hardware Lock, Antipiracy, Hard Drive Duplicators, HDD/SSD Duplicators, Portable Mini Duplicators, SATA HDD/SSD Duplicators, NVME M.2 PCIe SSD Duplicators, SAS Duplicators, CRU Duplicators, Duplication Solutions, Replication System, Cyber Security Hardware Keys, FIDO & FIDO2 Security Keys, Biometric + Fingerprint Security Keys, FIDO U2F authentication keys, FIDO U2F FIDO2 USB keys devices and multi-factor authentication keys, FIDO2 secure access keys, digital identity keys/2FA/MFA via encryption keys via FIDO/OTP Tokens for OTP authentication and PKI Tokens, Flash Duplicators, USB Drive Duplicators, USB 2.0 Duplicators, USB 3.0 Duplicators, SD & MicroSD Duplicators, CF/CFast Duplicators, SATA DOM Duplicator, CD/DVD Duplicator products and solutions for protecting cloud, data, and software and securing digital content.
Cyber Security Hardware Devices – Identity Security – Access Management
Buy Authentication Devices – FIDO & FIDO2 Security Keys, PKI Tokens, OTP Hardware, Smart Cards and Readers, Biometrics Hardware Products

OTP Hardware Tokens
- OTP Authentication
- OTP c100
- OTP c200
- OTP c200 NFC
- OTP c300 Challenge/Response (OCRA) Token
- E-signature OTP Token
- One Time Password (Token/Card)
- Event-Based OTP Token
- Time-Based OTP Token
- Single Button OTP Token
- QR Code OTP Token
- Mobile/Watch OTP Token
- Authentication System
- Seed Programming Suite

Smart Cards Products
- ePass Card
- Java Smart Cards PKI
- Campus Card
- BioCard
- Dual Interface FT-JCOS Java Card/Smart Card with CC EAL5+
- Java Card (A40CR)
- Java Card (A22CR PLUS)

Access Control Products
Access control products provide robust and scalable solutions for managing and securing physical access to facilities, systems, and resources.

Smart Card Reader
- Bluetooth Card Reader
- Contact Based Card Reader
- Contactless Card Reader
- Dual Interface Card Reader
- Mobile Dongle Reader
- Mobile Phone Sleeve Reader
- Tablet Sleeve Reader

Smart Payment Products
SmartPay Software
STORM Software
FT-405D Cashier Box
F68 Handheld Barcode Scanner
F26 2D Handheld Barcode Scanner
P10 Portable Printer
P20 Desktop Printer
P30 Desktop Thermal Printer

Power Card
- Fingerprint Card
- Event-Based (HOTP) OTP Card
- Time-Based (TOTP) OTP Card
HDD/SSD Duplicators – Hard Drive Duplicators
Portable HDD and SSD Duplicators – SATA HDD & SSD Duplicators – NVMe M.2 PCIe SSD Duplicators – SAS Duplicators – CRU Duplicators
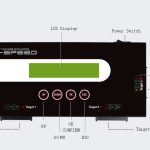
Portable HDD Duplicators
Our portable hard drive cloner/mini carry hdd copier device offers many different models. You can choose between 1 or 3 targets and three different speed performance options.

SATA HDD/SSD Duplicators
SATA hard disc cloner is the most economical way to duplicate 3,5″ SATA and 2,5″ SATA HDDs or SSDs.

NVME M.2 PCIe SSD Duplicators
M.2 NVME Duplicator is a Nvme disk cloner it the most economical M.2 Duplicators

SAS Duplicators
SAS cloner duplicator is created for the purpose of high-volume duplication of SATA/SAS HDDs.

CRU HDD Duplicators
CRU Duplicators Copier is a disk cloner for the digital cinema industry. CRU HDD duplicator is our solution to copy the CRU DX115 carriers. In the cinema industry movies can be distributed with a CRU DX115 carrier which holds the harddrive.

EZ Dupe NVMe SSD Duplicators
- NVMe CyCLONE 600 Duplicator (36GB/min)
- NVMe CyCLONE Pro 300 Duplicator (18GB/min)
- NVMe CyCLONE 300 Duplicator (18GB/min)
- Mini NVMe Plus Duplicator (45MB/s)
- NVMe Touch Duplicator (35MB/s)
- NVMe CyCLONE Printer

EZ Dupe SATA HDD/SSD Duplicators
- HD CyCLONE 600 Duplicator (36GB/min)
- HD Leopardo Duplicator (18GB/min)
- HD CyCLONE 300 Duplicator (18GB/min)
- HD CyCLONE II 300 Duplicator (18GB/min)
- HDmini Pro Touch – SATA II (18GB/min)
- HDmini Touch
- HD Pal Jr.
- HD Pal
- HD Pal Pro
- Computer Forensic Holmes 221B
- HD Pantera
- HD Leopardo
- HDmini
- HDmini Pro
- Adapter for Platform & Portable HDD Duplicator
Flash Duplicators
Standalone High-Speed Flash Media/Card/Storage Memory Duplicators

SATA DOM Duplicator
Professional SATA DOM Duplicators for Reliable Module Cloning
EZ Dupe USB Drive Duplicators
Standalone USB Duplicator: Copy, Erase, Quality Check

USB CyCLONE Duplicator for External HDD
- 1-15 USB CyCLONE Duplicator(45MB/s)

USB Pantera Duplicator
- 1-15 USB Pantera Duplicator
- 1-31 USB Pantera Duplicator
- 1-47 USB Pantera Duplicator
- 1-55 USB Pantera Duplicator
- 1-95 USB Pantera Duplicator
- 1-199 USB Pantera Duplicator

USB Touch Duplicator
- 1-10 USB Touch Duplicator

Mini USB Duplicator
- 1-4 Mini USB Plus Duplicator MK II (w/o LCM)
- 1-7 Mini USB Plus MKIII Duplicator (w/o LCM)
- 1-9 Mini USB Pro Duplicator (Blue LCM)
Software Protection – USB Dongles – Hardware Lock

Rockey4 Smart
R4 SMART is a software security dongle hardware lock product is based on smart-card chip card for multiple software program applications certied by EAL 4+ and IT SEC certification.

Rockey4ND
ROCKEY4ND is an advanced USB security device system for write complex algorithms securely stored in the dongle and algorithms in your application, is very difficult to crack, high levels of security.

Rockey2
R2 is a traditional dongle for application security and low cost. R2 dongle has a global unique hardware ID. Driverless under windows, Linux and mac OS. Shell encryption tool is provided to envelope EXE, DLL programs without extra developement work.

CopyLock
A CL USB Hardware Key (HASP) is a basic USB encryption dongle key, is a portable security device for software encryption and copy protection device that plugs into the USB port of the computer.
Copy Protection – Anti-piracy Solutions

USB Copy Protection Solutions
USB copy protection solutions protect files on removable storage devices from unauthorized copying, distribution, and alteration. These solutions can be software-based or hardware-based, offering various features like encryption, file binding, password protection, and write protection

Virtual Disk Copy Protection
Virtual disk copy protection involves using various software tools and techniques to prevent unauthorized duplication of data stored on virtual disks (like those used in virtual machines or virtual storage solutions). This protection aims to safeguard copyrighted software, data, or other sensitive information from being illegally copied and distributed

CD/DVD/BD Copy Protection
One Time Password (Token/Card) for Event-Based OTP, Time-Based OTP and One Time Password OTP Display Cards.

Video Editing Projects Copy Protection
PKI Tokens Authentication, Encryption and Digital Signatures by Public Key Infrastructure system.
Copy Protection Software
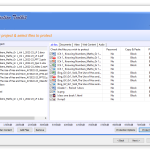
TSFD Protection Toolkit Software
TSFD Protection Toolkit is a powerful software encryption and anti-piracy tool that lets you secure data and duplicate copy protected digital content files on USB flash drives with industry-leading USB copy protection for video, audio, Microsoft Office documents, PDFs, offline web pages, and more.
Virtual Disk Protection Toolkit Software
Virtual Disk Protection Toolkit is a effortless Disk-less Copy Protection. Protect and distribute your content with the Virtual Disk Protection (VDP) Toolkit for video, audio, Microsoft Office documents, PDFs, offline web pages, and more..
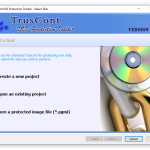
DVD Protection Toolkit Software
DVD Protection Toolkit is a software designed to protect nearly any file type on recordable CD, DVD, or Blu-ray discs. Protect your discs and your content with industry-leading DVD copy protection.
Smart CB Protection Toolkit Software
The “Smart CB viewer Protection Toolkit Software” is a toolkit used to protect the video, audio on usb drive for USB Copy Protection for Windows, Android TV, Mac, iOS on USB media through a Smart CB Viewer application.
Disc Duplicators
Optical Disc CD/DVD or Blu-ray Disc Duplicators and Duplication

USB to Disc Duplicator
- USB to Data Disc CD DVD Duplicator
- USB to Data Disc CD DVD BD Duplicators

MultiMedia Duplicator
- Multimedia Center – USB/SD/CF to CD/DVD Duplicator
- Multimedia Center USB/SD/CF to Blu-ray/CD/DVD Duplicator

MultiMedia Plus Duplicator
- Multimedia Center Plus Duplicator
- Multimedia Center Plus USB/SD/CF to Blu-ray/CD/DVD Duplicator

Daisy Chain Duplicator
- CD DVD SATA Daisy Chain Duplicator
- Blu-ray SATA Daisy Chain Duplicator

Rackmount CD DVD Duplicator
- Rackmount CD/DVD Duplicator
- Rackmount Blu-Ray/CD/DVD Duplicator

CD DVD Blu-Ray Burners
- LG Super Multi Internal Blu-ray CD DVD Writer
- Asus Super Multi Internal Blu-ray CD DVD Writer
- Lite-ON Super Multi Internal Blu-ray CD DVD Writer
- Plextor SATA DVD/RW Dual Layer Burner Drive Writer – Black (Bulk)

Media & Consumables
- CD Blank Media
- DVD Blank Media
- Blu-ray Blank Media

Application Security
Secure Your Applications and APIs with Modern Protection. As businesses embrace digital transformation, applications play a critical role in driving innovation and efficiency. However, traditional security methods often fall short in today’s fast-paced, ever-changing environments. Discover how our advanced application security solutions can help you protect your apps and APIs—anytime, anywhere.
Data Security
Comprehensive Data Security for a Connected World. No matter where your data resides—on-premises, in the cloud, or in transit—Aftindia provides powerful encryption and data protection solutions to safeguard your sensitive information. Rely on our proven strategies to prevent data breaches, ensure regulatory compliance, and keep your enterprise secure at every stage.


Identity Security & Access Management
Secure and Seamless Identity Security & Access Management. As your organization expands its use of cloud applications, ensuring secure and reliable access is more important than ever. Aftindia helps you simplify identity and access management by providing trusted, secure access to both cloud services and on-premises enterprise apps—empowering your employees to work safely from anywhere.
Smart Software Monetization
Maximize Revenue with Smart Software Monetization. Unlock the full value of your software with Aftindia’s advanced software monetization solutions. From flexible licensing models to robust IP protection, we help you optimize revenue streams, reduce piracy, and deliver a seamless user experience. Empower your business with tools that adapt to evolving customer needs and market demands.

We are driven by IT security hardware & cybersecurity solutions
IT security hardware, cybersecurity hardware, network security devices, firewalls, intrusion detection systems, hardware security modules, secure access devices, endpoint security hardware, data protection hardware, security appliance, hardware firewall, IT infrastructure security, physical security solutions, secure network hardware, IT asset protection
Security Solutions for Mobile
Aftindia offers a range of solutions to enable secure mobile working on smartphones and tablets.
Biometric Security Solutions
Data security and user authentication.
Software Copy Protection, Licensing and Anti-Piracy
Prevent Unauthorized Use of Your Software. Enforce the Terms of Your Software License, Preventing Reverse Engineering (IP Theft).
USB hardware key and licensing system.
Hardware-based security. Driverless. Multi-platform support.
Intelligent software copy protection and licensing solution with cloud-based admin controls.
Anti-piracy solutions and licensing system with cloud-based intelligent monitoring. Flexible licensing. Intelligent monitoring. Web-based administration.
User Access Control.
Prevent Unauthorized Access to Systems and Applications.
Identity and Access Management (IAM)
Allocate Permissions. Identity Access Management (IAM) systems enable the control of users’ permissions to be maintained.
Software Monetization Solutions
Software monetization solutions from Aft India help businesses secure the return on investment they are due from their software distribution without fear of losing out to software pirates.
Automatic Software Protection
Aftindia’s Shell method is a simple way to automatically add copy protection to your software without having to modify the source code. Code is automatically added to your software which locks it to a license inside a security key.
Software Copy Protection, Licensing and Anti-Piracy
Prevent Unauthorized Use of Your Software. Enforce the Terms of Your Software License, Preventing Reverse Engineering (IP Theft).
Software protection dongle-based secure software distribution and licensing system.
Hardware-based security. Driverless. Multi-platform support.
Intelligent software copy protection and licensing solution with cloud-based admin controls.
Software security solutions and licensing system with cloud-based intelligent monitoring. Flexible licensing. Intelligent monitoring. Web-based administration.
Multi-Factor Authentication System
We protects access to websites, workstations and networks by providing more secure logins.
Featured Solutions

Industry Security Solutions
Learn more about the different cyber-physical solutions relevant for your industry.

Cyber-Protection Solutions
Explore solutions to prepare for and protect against cyber-attacks.

Cyber-Attack Solutions
Learn more about how to prevent and manage cyber-attacks.

Smart Payment Solutions
Learn more about on how to enable contactless payments and enhance transaction security.
Not Sure What Product Is Right For Your Company?
Learn more about the solutions AFT INDIA offers to find the best fit security solution for your use case.
How to Purchase
To explore and purchase AFT India’s cybersecurity hardware solutions, you can visit their official website: AFT India Cybersecurity Products. For personalized assistance or to request a demo, consider reaching out to their sales team directly through the contact information provided on their site.
If you need further information or assistance in selecting the right product for your specific requirements, feel free to ask!




